Episode 10 - The Bit, The Seed, and the Paradox of Data Flow
Failed to add items
Add to basket failed.
Add to Wish List failed.
Remove from Wish List failed.
Follow podcast failed
Unfollow podcast failed
-
Narrated by:
-
By:
About this listen
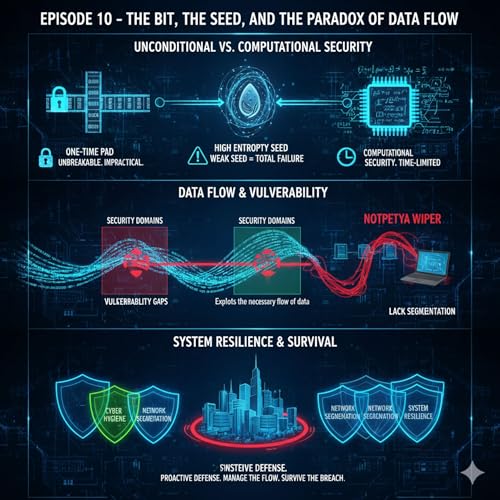
This episode begins by exploring the cryptographic ideal of unconditional security, which is only truly achieved by the theoretical One-Time Pad (OTP), a cipher that is mathematically unbreakable. The impracticality of the OTP lies in the difficulty of creating, distributing, and securely managing a perfectly random, one-time key as long as the message. This logistical challenge forces most of the digital world to rely on computational security, which uses strong algorithms that are merely too time-consuming and resource-intensive to break in a practical timeframe. The security of these modern ciphers is entirely dependent on the quality of the random numbers—the seed—used for key generation.
The discussion shifts to the fragility of pseudo-random number generators (PRNGs), which stretch a small, truly random seed into a long sequence of seemingly random bits, noting that a weakness in the initial seed compromises the entire sequence. The security of a digital system is shown to be a paradox: it relies on locking data down with encryption, yet its fundamental purpose is to enable the flow of data. This necessary movement of data, however, creates points of vulnerability, where an attacker can exploit the gaps between security domains. These weaknesses are often leveraged by modern malware, such as the destructive NotPetya wiper, which used sophisticated techniques to move from one system to another.
The NotPetya attack illustrates the devastating real-world consequences of poor system architecture, where the speed and breadth of the attack were magnified by a lack of network segmentation and inadequate patch management. Ultimately, the security of any system is defined by its weakest link, demonstrating that even the most robust algorithms cannot compensate for failures in basic cyber hygiene and overall system design. The episode concludes by advocating for a defensive strategy that recognizes this paradox, focusing on robust system resilience and the proactive management of data flow to survive inevitable compromise.



